

When you create a Touchpoint Security policy, you do not directly identify the operators that act on touchpoints you want to secure. Instead, you identify the categories to which those operators belong. You identify the categories, not by name, but by Access Control ID.
Not all categories contain operators that could compromise the security of a host with sensitive information. Evaluate the impact of operators before adding resources.
You can identify the Access Control ID to add as a resource to a Touchpoint Security policy.
Follow these steps:
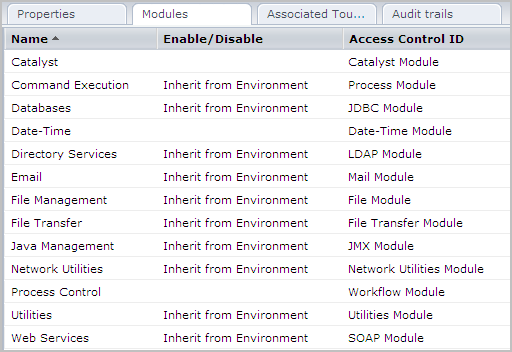
Important! The Access Control ID column lists module names. Refer to this list when you enter selected module names in the Resources field in a Touchpoint Security policy.
|
Copyright © 2014 CA.
All rights reserved.
|
|